A U.S.-based cybersecurity intelligence group says Iranian state institutions have perpetrated a growing number of international cyberattacks for profit in recent months.
In a VOA Persian interview, Accenture Security growth and strategy leader Tom Parker said most cyberattacks attributed by his research team to Iran's Islamic Revolutionary Guard Corps (IRGC) and similar state bodies were financially motivated. The Arlington, Virginia-based company published a report Tuesday saying research conducted since the start of this year indicates that Iranian state hackers used several ransomware tools to carry out those for-profit cyberattacks.
"We certainly have seen an evolution in the motive of why some attacks are initiated," said Parker, referring to findings in Accenture Security's 2018 Cyber Threatscape Report that examines international trends in cyber threats. "Nation states, Iran included, have realized that cyberattacks are not just about stealing intellectual property or sending a political message or causing an outage on a critical system. They also can take a page out of the organized criminals' book and make some significant money out of cyberattacks to fund their own non-cyber programs."
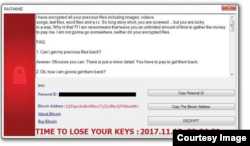
In the report, Accenture Security's iDefense threat intelligence team said it identified five ransomware variants as having been developed or repurposed in Iran: RASTAKHIZ, TYRANT, WannaSmile, Black Ruby and Android ransomware. It said Iran-based cybercriminals who created or modified those variants have shared data with the IRGC for future research and development.
‘Growing force’
Iranian officials repeatedly have denied accusations of involvement in hacking attacks against the United States and Gulf Arab nations in recent years. The U.S. and its Sunni Gulf allies long have sought to push back against Shiite-majority Iran for what they see as its aggressive efforts to dominate the Middle East.
The Accenture Security report described the "Iranian [cyber] threat" as a "growing force" that is most likely to target nations such as Saudi Arabia, the United Arab Emirates, Bahrain and Israel. But it also said Iran is unlikely to carry out any disruptive or destructive cyberattacks against the U.S. or its European allies in the near future. The report said the Trump administration's May withdrawal from the 2015 Iran nuclear deal has put Tehran in what it called a "defensive" position toward the West.
The Trump administration reimposed several financial sanctions against Iran on Tuesday, to try to pressure Iran into making a new deal that would permanently end what Washington sees as Tehran's nuclear weapons ambitions. Parker said his team has not seen any signs of Iran retaliating for those sanctions by launching cyberattacks against U.S. targets. Iran denies seeking nuclear weapons.
Parker said another reason for the U.S. not being a likely Iranian cyber target in the near term is that any meaningful damage to U.S. infrastructure would require increased cyber capabilities. But he said Iran is moving gradually toward developing such abilities.
"While we have not seen a huge attack against, let's say, the power grid in the U.S., many nation states such as Iran do continue to demonstrate a desire to learn more about our critical infrastructures," Parker said. "There is definitely a sense that nation states including Iran are playing the long game and are preparing the battlefield so that certain capabilities might be at their disposal in the future."
This report was produced in collaboration with VOA's Persian service.