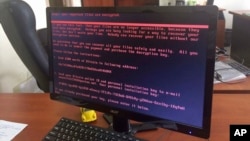
Computers around the world were locked up and users' files held for ransom in a cyberattack Tuesday that paralyzed some hospitals, government offices and major multinational corporations.
Here's a look at how malware and ransomware work and what people can do if they fall victim to attacks.
What is malware and ransomware?
Malware is a general term that refers to software that's harmful to your computer, says John Villasenor, a professor at the University of California, Los Angeles. Ransomware is a type of malware that essentially takes over a computer and prevents users from accessing data on it until a ransom is paid, he says.
How does your computer become infected with ransomware?
In most cases, the software infects computers through links or attachments in malicious messages known as phishing emails.
"The age-old advice is to never click on a link in an email," said Jerome Segura, a senior malware intelligence researcher at Malwarebytes, a company based in San Jose, California, that has released anti-ransomware software. "The idea is to try to trick the victim into running a malicious piece of code."
The software usually is hidden within links or attachments in emails. Once the user clicks on the link or opens the document, their computer is infected and the software takes over.
But some of the major ransomware attacks recently, including last month's WannaCry and the one spreading Tuesday, borrowed leaked National Security Agency code that permits software to spread quickly within an organization's network.
How ransomware works
"Ransomware, like the name suggests, is when your files are held for ransom," said Peter Reiher, a UCLA professor who specializes in computer science and cybersecurity. "It finds all of your files and encrypts them and then leaves you a message. If you want to decrypt them, you have to pay."
The ransomware encrypts data on the computer using an encryption key that only the attacker knows. If the ransom isn't paid, the data is often lost forever.
When the ransomware takes over a computer, the attackers are pretty explicit in their demands, Segura says. In most cases, they change the wallpaper of the computer and give specific instructions telling the user how to pay to recover their files.
Most attackers demand $300 to $500 to remove the malicious ransomware; the price can double if the amount isn't paid within 24 hours. The demand in Tuesday's attack was $300 per computer, according to security researchers.
Law enforcement officials have discouraged people from paying these ransoms.
How to avoid these attacks
The first step is being cautious, experts say. Users should also look for malicious email messages that often masquerade as emails from companies or people you regularly interact with online. It's important to avoid clicking on links or opening attachments in those messages, since they could unleash malware, Villasenor says.
But Villasenor says there is "no perfect solution" to the problem.
Users should regularly back up their data and ensure that security updates are installed on your computer as soon as they are released. Up-to-date backups make it possible to restore files without paying a ransom.
WannaCry and Tuesday's attack exploited vulnerabilities in some versions of Microsoft Windows. Microsoft has released software patches for the security holes, although not everyone has installed those updates.
Even so, the new malware appears to have a backup spreading mechanism, so that even if some computers were patched, they can still be hit if one or more machines in a network weren't patched.