As the World Wide Web has evolved and grown more complicated, so have the tools and techniques of cyber-espionage and military action.
Perhaps nowhere is this evolution more clearly seen than in China’s recently disclosed “Great Cannon” and its similarities to a tool reportedly possessed by the United States known as “QUANTUM.”
Depending on how they are wielded, both can serve as a high-tech tool for spies, intimidating weapons of cyberassault, or a combination of both, analysts say.
In March, the operators of GitHub – a popular site among software developers – noticed something unusual. Two open-source project sites on GitHub, both aimed at circumventing Chinese censorship of the Web, were under a heavy and sustained DDoS attack.
The attack itself wasn’t all that surprising: the hosted sites GreatFire and a mirror copy of the New York Times in Mandarin had long been irritants to Chinese cyber officials. What was different this time is that much of the traffic appeared to be coming from computers outside the Great Firewall – many within the U.S., they said.
The attacks lasted for more than a week, and not only took the two targets offline but seriously crippled GitHub.
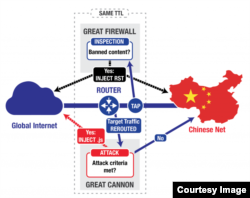
In April, researchers at the University of Toronto’s “Citizen Lab” confirmed that it was indeed something new – and something powerful. Dubbed “The Great Cannon,” it’s a tool that Chinese officials could use for censorship, espionage, or worse.
"The operational deployment of the Great Cannon represents a significant escalation in state-level information control: the normalization of widespread use of an attack tool to enforce censorship by weaponizing users," the researchers wrote.
“The Great Cannon is not simply an extension of the Great Firewall, but a distinct attack tool that hijacks traffic to (or presumably from) individual IP addresses, and can arbitrarily replace unencrypted content as a man-in-the-middle [attack.]”
And it has the Obama administration wary.
US closely watching
Jeff Rathke, acting deputy spokesperson for the State Department, said any effort to censor the Web or use it in an offensive fashion is troubling.
“We are concerned by reports that China has used a new cyber capability to interfere with the ability of worldwide Internet users to access content posted outside of China,” Rathke said.
“The cyberattack manipulated international Web traffic intended for one of China’s biggest Web-services companies and turned it into malicious traffic directed at U.S. sites," he said last week. “We have asked Chinese authorities to investigate this activity and provide us with the results of their investigation.”
For well over a decade, Chinese officials have routinely blocked access from within China to a variety of websites, typically for hosting content that is critical of Beijing or its policies, using something often called "The Great FireWall of China."
The Great Firewall, or GFW, uses a mesh of active and passive filters that can scan for keywords in messages and search requests. Keywords deemed “triggers” reroute Web traffic away from banned pages and either to government-approved sites or into the oblivion of cyberspace.
The Great Cannon uses the GFW’s existing infrastructure, but then weaponizes global Web traffic into a focused, offensive system.
In its first use, the Great Cannon was used to censor sites Beijing finds troublesome.
But cyber-researcher and report co-author Nicholas Weaver says censorship is the least of the threats posed by the device.
“It was basically big and showy, but not very effective,” he said, warning that with little modification the Great Cannon could take on powerful offensive capabilities.
“I could modify it, for example, to intercept all emails coming from China directed to a target,” he said. “If there happens to be an email to my target with a Word document, I could modify that Word document to contain an exploit, which would be effectively unnoticeable to everybody.”
US fights back
But China isn’t alone in possessing such advanced cybertools.
A full year before the Great Cannon’s launch, in March 2014, journalists Ryan Gallagher and Glenn Greenwald published a lengthy report on a series of classified programs run by the U.S. National Security Agency, the details of which were leaked by former NSA contractor Edward Snowden.
Among those programs are several that allegedly operate under the name QUANTUM.
Citing the leaked NSA documents, Gallagher and Greenwald detail QUANTUM’s ability to conduct DNS, MySQL and HTTP injection, which potentially would allow the NSA to alter or destroy a target’s databases, employ botnets for sustained attacks, and even reroute Web traffic to phony NSA-sponsored sites.
That makes QUANTUM a powerful bundle of tools that could, conceivably, allow the NSA near-complete access and control of a target’s computer systems.
Queries from VOA to the NSA for comment about the existence of QUANTUM were not returned.
But Citizen Lab researchers, in their report on the Great Cannon, noted similarities between the Great Cannon and QUANTUM.
“While employed for a highly visible attack in this case, the Great Cannon clearly has the capability for use in a manner similar to the NSA’s QUANTUM system, affording China the opportunity to deliver exploits targeting any foreign computer that communicates with any China-based website not fully utilizing HTTPS,” researchers wrote.
The powerful Web tools go to the heart of an emerging debate of whether they are espionage tools or offensive weapons.
“Neither,” said Bruce Schneier, a longtime crypto-analyst and chief technology officer at the cybersecurity firm Resilient Systems. “There’s no difference anymore.”
Schneier and others say that techniques used in the Great Cannon and QUANTUM aren’t new. In his book “Data and Goliath,” Schneier writes that the technology has been available on the market for years.
“The cyberweapons manufacturer Hacking Team sells packet injection technology to any government willing to pay for it,” Schneier wrote. “Criminals use it. And there are hacker tools that give the capability to individuals as well. All of these existed before I wrote about QUANTUM. By using its knowledge to attack others rather than to build up the Internet's defenses, the NSA has worked to ensure that anyone can use packet injection to hack into computers.”
Schneier says the boundary between cyber-espionage and cyberattacks is gone, and that “as long as cyber-espionage equals cyberattack, we would be much safer if we focused the NSA's efforts on securing the Internet from these attacks.”
Researcher Weaver told VOA that, while QUANTUM may have more in common with the GFW than the Great Cannon, these tools – whether used for espionage or censorship or something else – are essentially weapons.
"The Great Cannon is explicitly an offensive weapon, it just was used here to further their censorship goals," Weaver said. "The actual Cannon design is not constructed to efficiently block banned content, but rather its designed to explicitly hijack remote computers."
And, Weaver said, there’s only really one way to protect anyone’s computers or communications from being attacked.
“Encrypt everything,” Weaver said. “Every unencrypted website or communication is a vulnerability if your adversary can see the traffic and knows it’s coming from you. That’s the fundamental problem; we need to encrypt everything, all the time, as a matter of self-defense.”